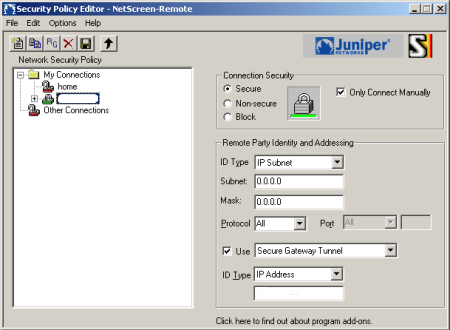
If you’ve configured your Juniper NetScreen-Remote VPN to route all your traffic through your VPN tunnel, you’ll find you get stuck when accessing local IPs on your (home) network, such as a NAS, printers, computer shares, …
This is usually how it’s configured in the Security Policy Editor.
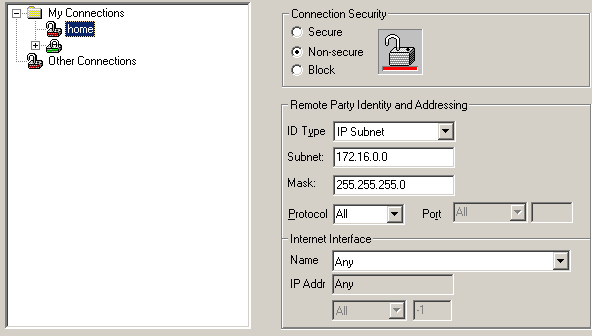
If you want to keep having access to your local IP range(s), create a new connection under “My Connections” and add it as follows.
Choose the following configuration settings.
- Connection Security: Non-secure
- ID Type: IP Subnet
- Subnet: 172.16.0.0
- Mask: 255.255.255.0
- Protocol: All
- Interface Name: Any
It goes without saying you you replace “172.16.0.0” with the IP range you want to have direct access to. Credits to David Geens for pointing it out!