As announced in September 2014, Chrome version 42 will start to block mark SSL connections using the SHA-1 algorithm as insecure, with a big red cross in the browser.
Update #1: this article originally mentioned Chrome blocking SHA-1 certificates. Chrome will mark them as insecure, but won’t actively block the connection. More in the post below.
Update #2: Chrome 42 is now the default and is auto-updated on all clients. SHA-1 certificates are now marked as insecure. (Chrome Release Blog: the Stable channel has been updated to 42.0.2311.87)
Chrome v42 is now publicly released. The browser now starts marking SSL certificates that still use the SHA-1 algorithm as insecure with a big red cross.
The web browsed with Chrome beta is a scary place. (Since v42 SHA-1 certs valid past 2015 are marked insecure.) pic.twitter.com/cLSNFJxOQH
— Filippo Valsorda (@FiloSottile) April 7, 2015
What is valid on Chrome 41, isn’t on Chrome 42. The xkcd.com site is a prime example. Here’s the site on Chrome 41.
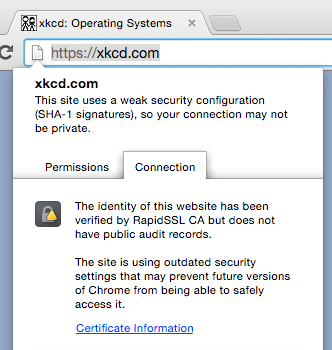
That same site is showing SSL certificate errors on Chrome 42.
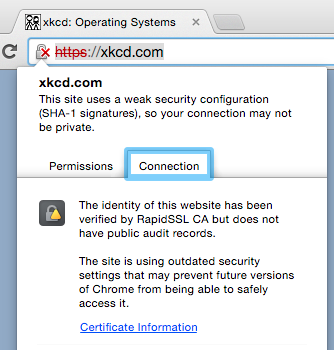
If you haven’t already, check your certificates. If they’re still using the SHA-1 algorithm, ask your SSL provider for a re-issue (hopefully free of charge) using a SHA-256. There are some additional rules on when SHA-1 certs are blocked shown as insecure, and when they aren’t, depending on the expiration date.
The tl;dr: only SHA-1 certificates with a validation date > 2015 are reported as insecure.
The problem is, it’s not only your certificate that needs to stop using SHA-1. Every intermediate needs to be updated as well. In the case of XKCD’s site, their certificate was correctly using a SHA-256 algoritme, but their intermediate isn’t.
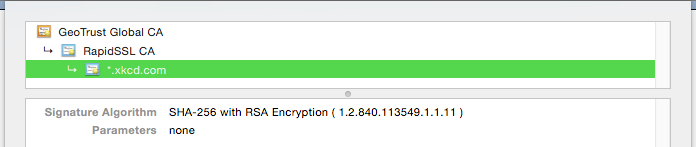
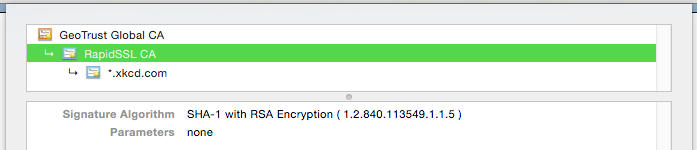
Better check your certificate chains!
As I’ve said before, the chain of trust is only as strong as its weakest link.