As it stands, the HTTPs “encrypted web” is built on trust. We use browsers that trust that Certificate Authorities secure their infrastructure and deliver TLS certificates (1) after validating and verifying the request correctly.
It’s all about trust. Browsers trust those CA root certificates and in turn, they accept the certificates that the CA issues.
Update: it’s less bad than it sounds, see comments below .
(1) Let’s all agree to never call it SSL certificates ever again.
Revoking trust#
Once in a while, Certificate Authorities misbehave. They might have bugs in their validation procedures that have lead to TLS certificates being issued where the requester had no access to. It’s happened for Github.com, Gmail, … you can probably guess the likely targets.
When that happens, an investigation is performed – _in the open _– to ensure the CA has taken adequate measures to prevent it from happening again. But sometimes, those CA’s don’t cooperate. As is the case with StartCom (StartSSL) and WoSign, which in the next Chrome update will start to show as invalid certificates.
Google has determined that two CAs, WoSign and StartCom, have not maintained the high standards expected of CAs and will no longer be trusted by Google Chrome, in accordance with our Root Certificate Policy.
This view is similar to the recent announcements by the root certificate programs of both Apple and Mozilla .
So Apple (Safari), Mozilla (Firefox) and Google (Chrome) are about to stop trusting the StartCom & WoSign TLS certificates.
From that point forward, those sites will look like this.
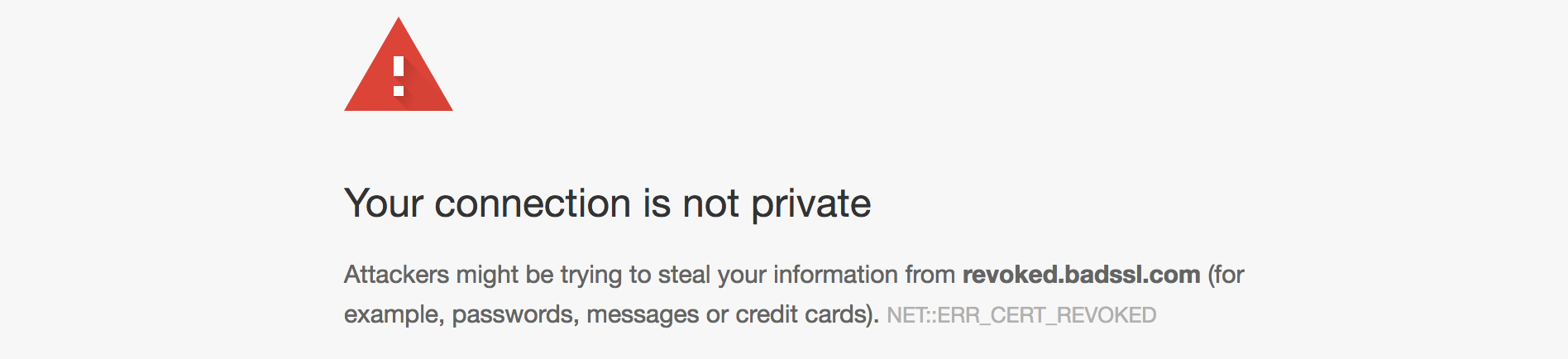
With Mozilla, Chrome & Safari, that’s 80% of the browser market share blocking those Certificate Authorities.
Staged removal of CA trust#
Chrome is handling the update sensibly, it’ll start distrusting the most recent certificates first, and gradually block the entire CA.
Beginning with Chrome 56, certificates issued by WoSign and StartCom after October 21, 2016 00:00:00 UTC will not be trusted. [..]
In subsequent Chrome releases, these exceptions will be reduced and ultimately removed, culminating in the full distrust of these CAs.
If you purchased a TLS certificate from either of those 2 CAs in the last 2 months, it won’t work in Chrome, Firefox or Safari.
Customer Transparency#
Those 3 browsers have essentially just bankrupted those 2 CA’s. Surely, if your certificates are not going to be accepted by 80% of the browsers, you’re out of business – right?
Those companies don’t see it that way, apparently, as they still sell new certificates online.
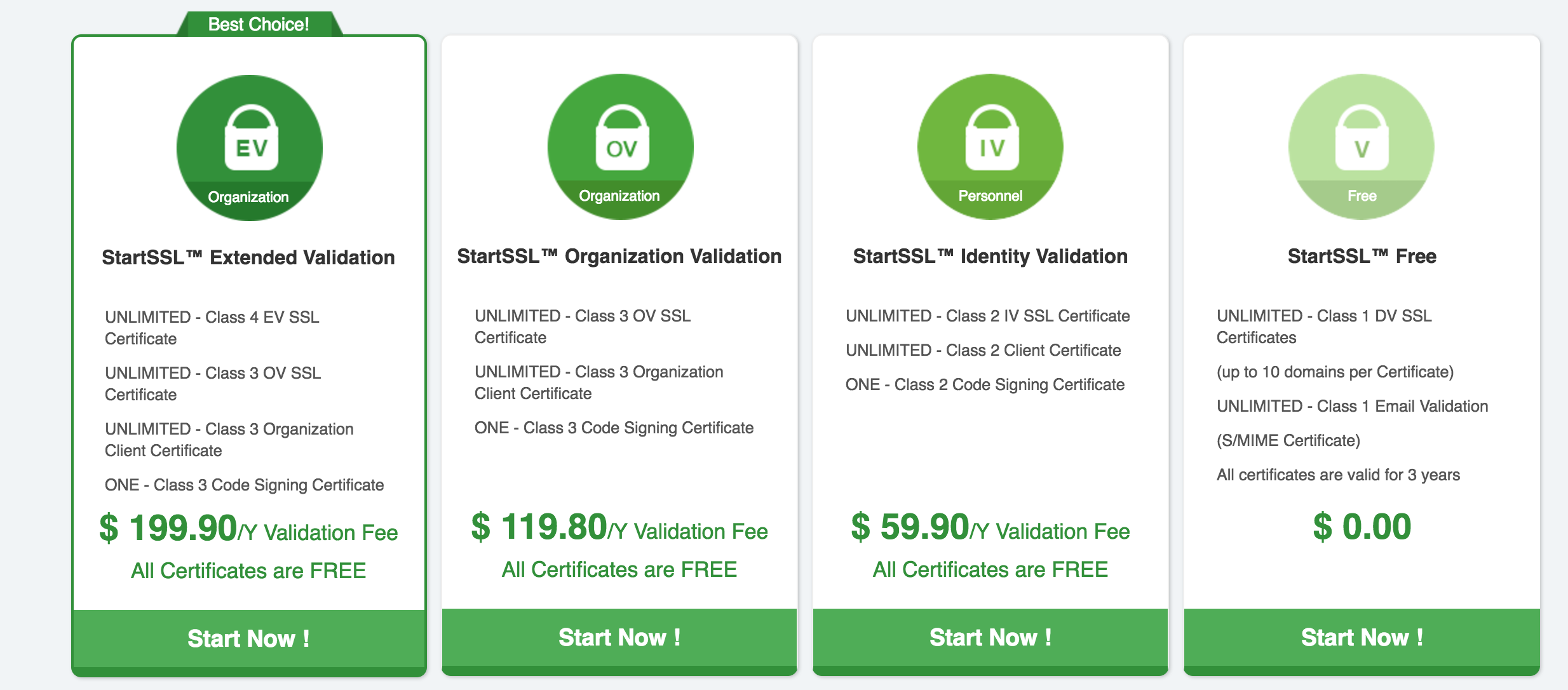
This is pure fraud: they’re willingly selling certificates that are known to stop working in all major browsers.
Things like that piss me of, because only a handful of IT experts know that those Certificate Authorities are essentially worthless. But they’re still willing to accept money from unsuspecting individuals wishing to secure their sites.
I guess they proved once again why they should be distrusted in the first place.
Guilt by Association#
Part of the irony is that StartCom, which runs StartSSL, didn’t actually do anything wrong. But a few years ago, they were bought by WoSign. In that process, StartCom replaced its own process and staff with those of WoSign, essentially copying the bad practices that WoSign had.
If StartCom hadn’t been bought by WoSign, they’d still be in business.
I’m looking forward to the days when we have an easy-to-use, secure, decentralized alternative to Certificate Authorities.