The internet is verbally attacking WordPress again. I read a lot of hate towards WordPress for its latest security vulnerabilities that have become public.

What I don’t see is praise in how those updates are handled and distributed to its millions of users.
Cross-Site Scripting Vulnerabilities#
The last 2 weeks, 3 major security releases have been announced by the WordPress team;
- 21/04/2015: version 4.1.2 fixes a critical cross-site scripting vulnerability
- 27/04/2015: version 4.2.1 fixes a cross-site scripting vulnerability
- 07/05/2015: version 4.2.2 fixes a cross-site scripting attack
Oh my, WordPress must pose a security risk, right?!
The Magical Release: WordPress 3.7#
I was skeptical when they first announced this, but automatic background updates as featured in the 3.7 release are amazing.
Automatic background updates were introduced in WordPress 3.7 in an effort to promote better security, and to streamline the update experience overall. By default, only minor releases – such as for maintenance and security purposes – and translation file updates are enabled on most sites. In special cases, plugins and themes may be updated.
If you read the comments on Twitter, security blogs and even major news sites, you would expect the internet to have crashed and burned by now, with all the WordPress security vulnerabilities.
But that magical feature saved the internet from a lot of problems. That feature, that most WordPress users take for granted, is the single best thing ever to happen to WordPress.
And to think I questioned it at launch. What happens when your auto-update breaks all sites? What happens if an update is pushed, that introduces more vulnerabilities or backdoors? What if WordPress.org is every compromised and attackers can influence that update?
None of those scenarios happened. At least, not yet. But WordPress’ trackrecord is solid.
Patching several million websites#
WordPress is popular. It powers millions of sites. Small & big. This puts it in a position where it’s bound to attract some unwanted attention. Once a critical WordPress vulnerabilty comes out, the update is pushed to those millions of sites within hours.
Hours.
Let that sink in for a while. After a few hours, WordPress administrators that left the auto-update enabled (which it is, by default), receive an e-mail like this.
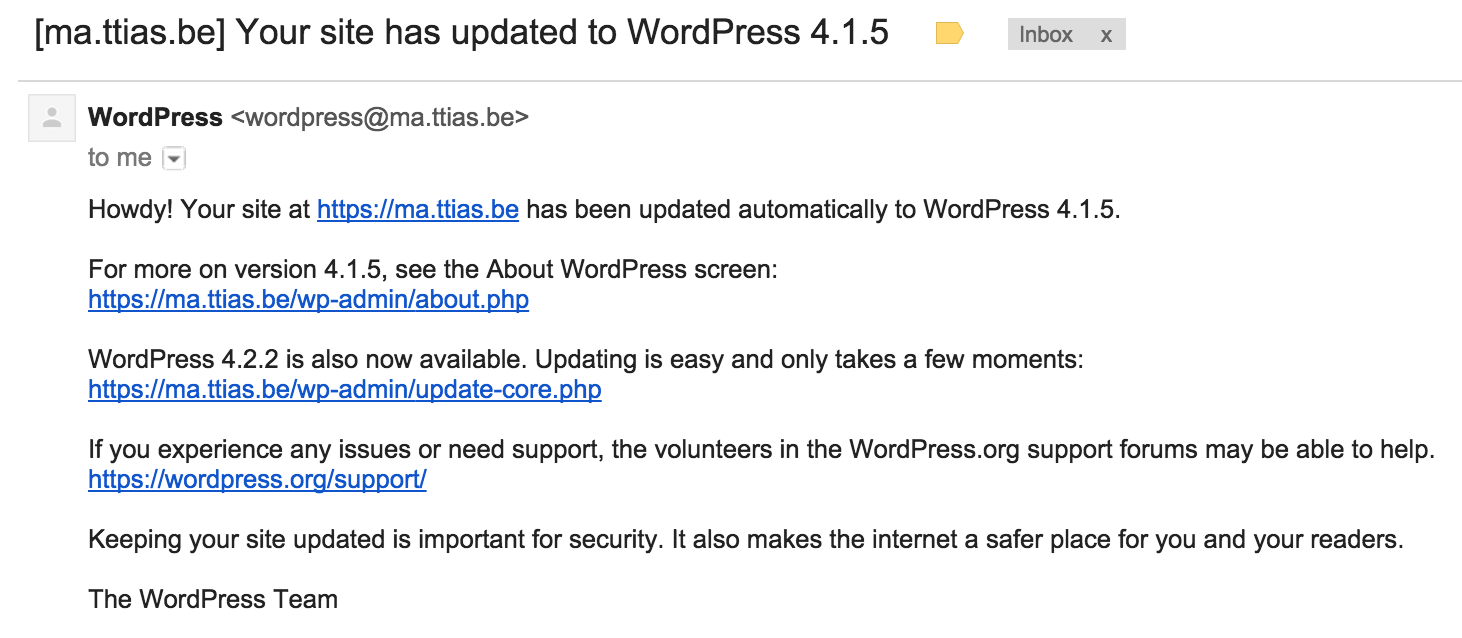
Just to put that into perspective, the steps to update Drupal core contain 13 instructions, among which;
Delete all the files & folders inside your original Drupal instance except for /sites folder and any custom files you added elsewhere.
Copy all the folders and files except /sites from inside the extracted Drupal package [tar ball or zip package] into your original Drupal instance.
WordPress users get that automatically.
Disabled auto-updates? Just log in and click a single button.
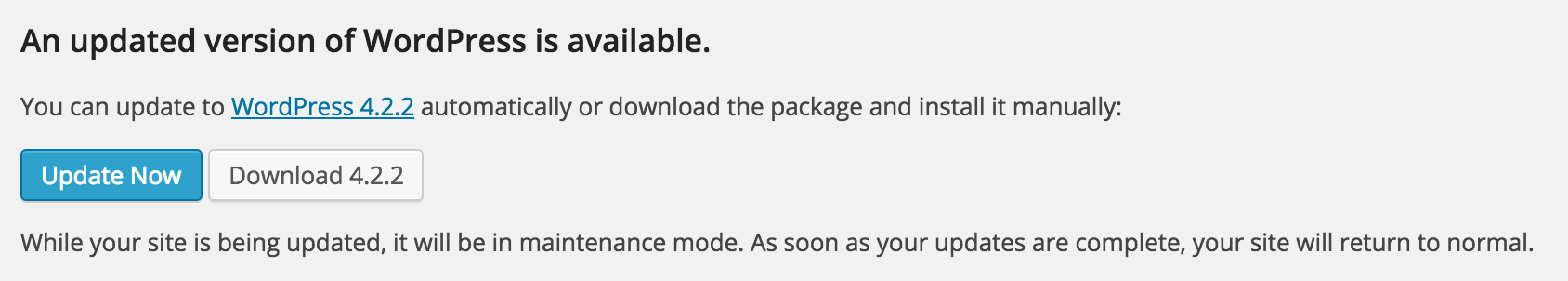
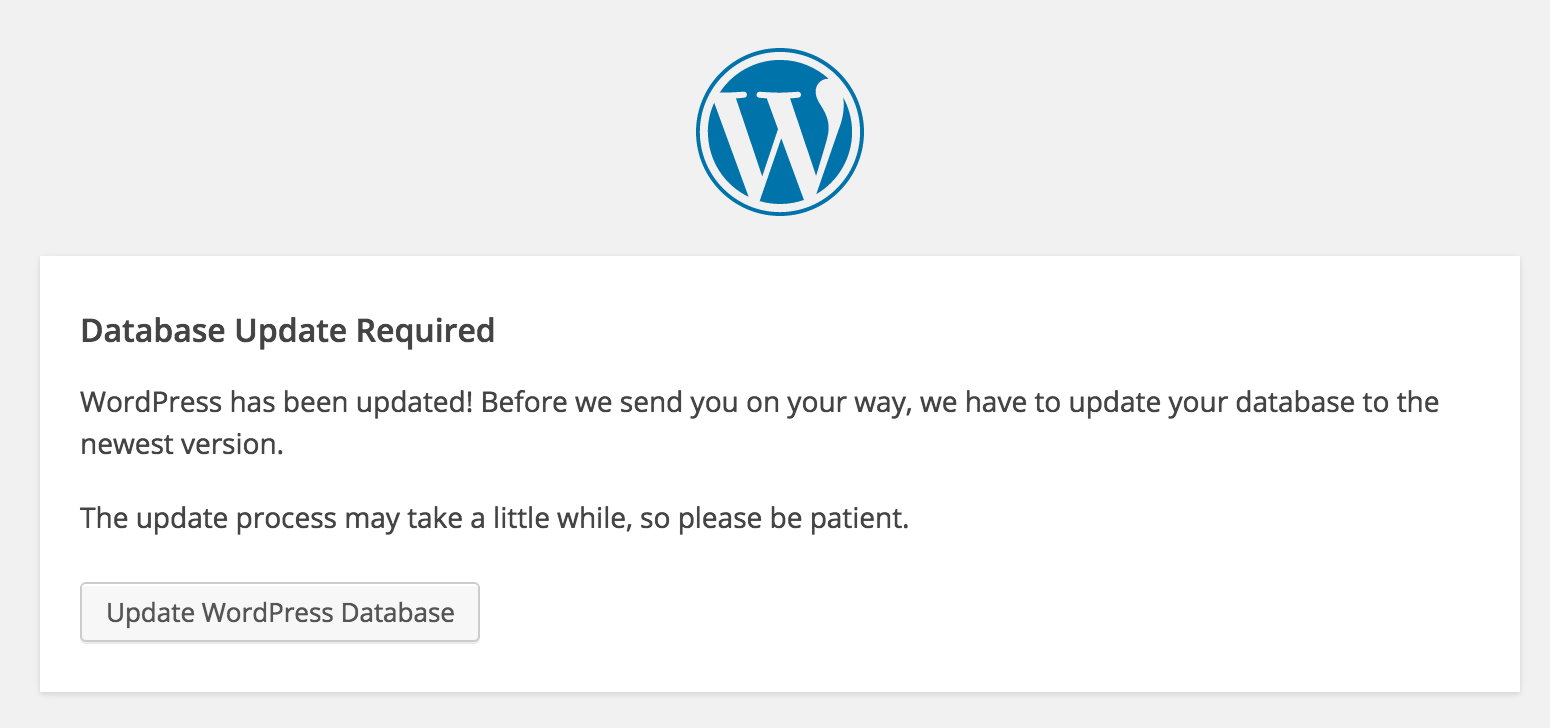
Does the update need a database schema change or upgrade? A single button.
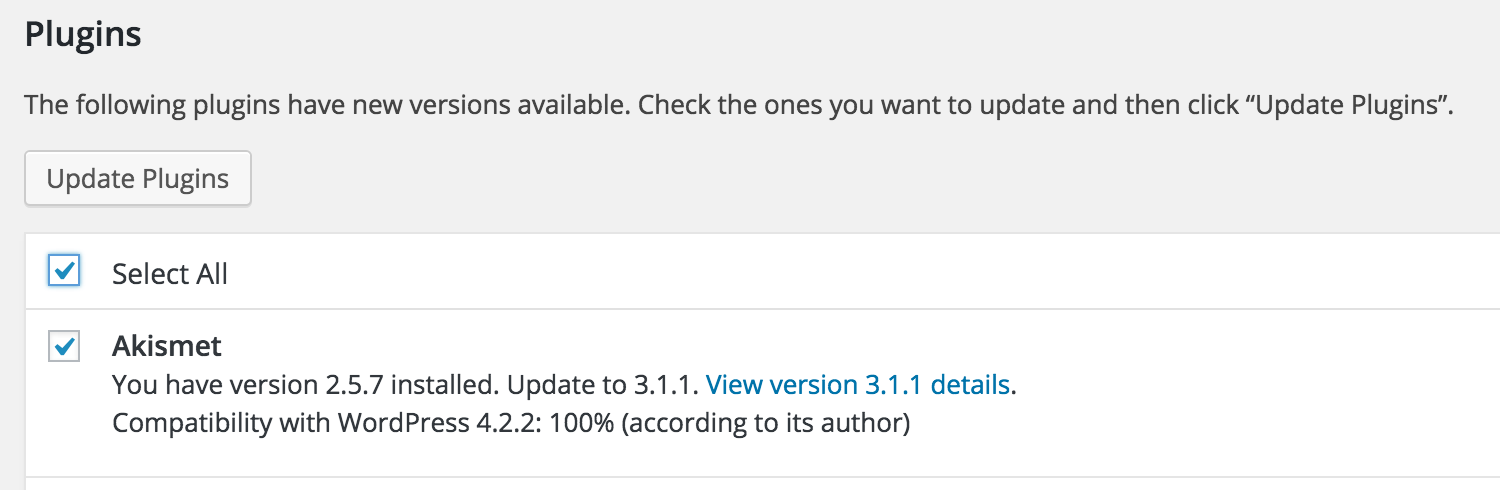
Want to updates your installed plugins, to the latest version? A single button.
Your themes? A single button.
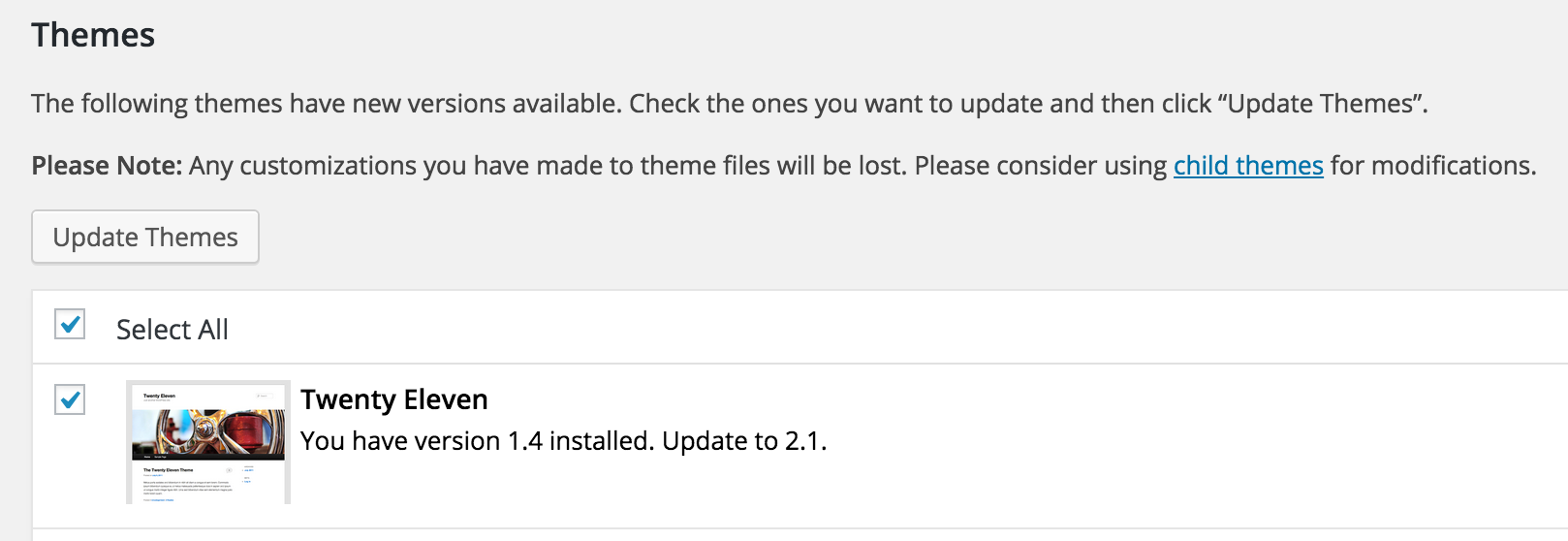
Let that sink in for a while.
The Punching Bag#
At PHP conferences, WordPress often serves as a punching bag.
Nearly every talk that discusses code quality brings in WordPress and compares it to other frameworks. WordPress always ends up at the bottom.
Yet here it is, powering the internet. Patching millions of sites in less than 24 hours.
As much as I appreciate the other frameworks, WordPress is by far the best at handling security incidents. Magento? Don’t get me started. Drupal? Your average user has no idea how to apply patches. I’m certain Drupalgeddon did far more damage than the recent 3 WordPress vulnerabilities, combined.
Joomla? Typo3? Each and every one can learn from WordPress.
Thanks, WordPress#
I for one would like to thank WordPress. Besides powering this blog, it powers thousands of our clients . And thanks to this auto-update feature, each and every one of those is safer.
For all the hate the internet redirects to WordPress and for all the punches it has to take, I think there’s far too little appreciation for everything WordPress does.
Thanks guys, keep it up.
WordPress is taking *a lot* of critique for its 3 XSS exploits. I think it deserves praise, for how it handled them. https://t.co/BtxICTKrjg
— ma.ttias.be (@mattiasgeniar) May 7, 2015