As announced at the beginning of this week , OpenSSL has released the fix for CVE-2015-1793.
These releases will be made available on 9th July. They will fix a single security defect classified as “high” severity. This defect does not affect the 1.0.0 or 0.9.8 releases.
More details and how to patch can be found below.

High Severity Patch#
The patch is considered a high severity patch. The details are as follows, as published by the OpenSSL team.
During certificate verification, OpenSSL (starting from version 1.0.1n and 1.0.2b) will attempt to find an alternative certificate chain if the first attempt to build such a chain fails.
An error in the implementation of this logic can mean that an attacker could cause certain checks on untrusted certificates to be bypassed, such as the CA flag, enabling them to use a valid leaf certificate to act as a CA and “issue” an invalid certificate.
This kind of vulnerability allows man-in-the-middle attacks and could cause applications to see invalid and untrusted SSL certificates as valid. It essentially allows everyone to be come their own Certificate Authority (CA).
The bug is fixed in commit aae41f8c54257d9fa6904d3a9aa09c5db6cefd0d .
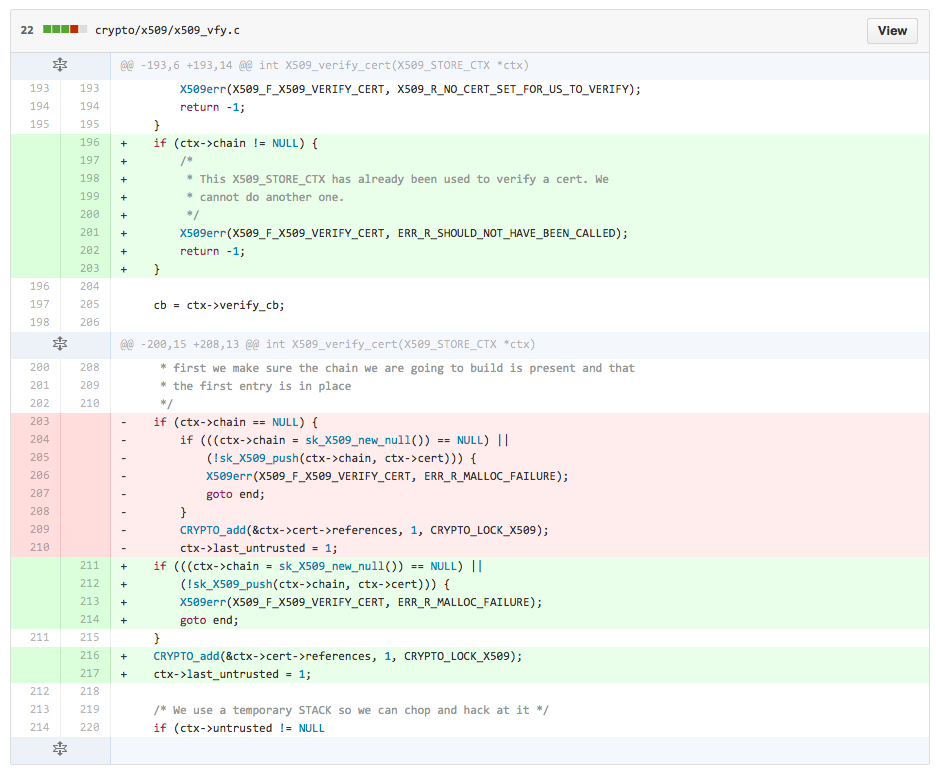
And in commit 2aacec8f4a5ba1b365620a7b17fcce311ada93ad .
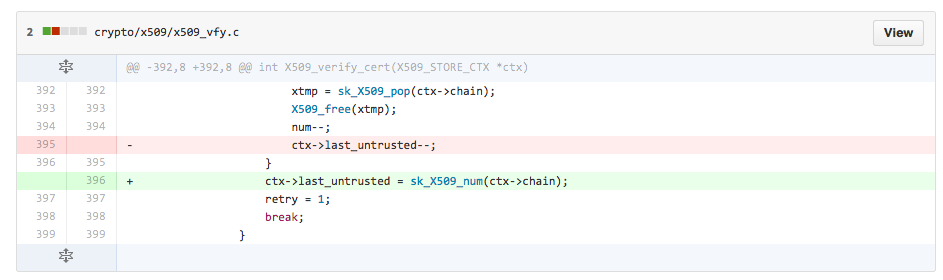
Pretty damn serious, indeed. That means it’s patching time again.
The “upside” is that it only affects a limited set of OpenSSL versions: OpenSSL versions 1.0.2c, 1.0.2b, 1.0.1n and 1.0.1o.
Which versions & operating systems are affected?#
The vulnerability appears to exist only in OpenSSL releases that happened in June 2015 and later. That leaves a lot of Linux distributions relatively safe, since they haven’t gotten an OpenSSL update in a while.
Red Hat, CentOS and Ubuntu appear to be entirely unaffected by this vulnerability, since they had no OpenSSL updates since June 2015.
As confirmed by Red Hat ’s announcement :
The OpenSSL project has published information about an important vulnerability (CVE-2015-1793) affecting openssl versions 1.0.1n, 1.0.1o, 1.0.2b, and 1.0.2c. These upstream versions have only been available for a month, and given Red Hat’s policy of performing careful backports of important bug fixes and selected features, this functionality is not present in any version of OpenSSL shipped in any Red Hat product.
No Red Hat products are affected by this flaw (CVE-2015-1793), so no actions need to be performed to fix or mitigate this issue in any way.
Just to be on the safe side, check for package updates and apply them ASAP if they’re available. Especially if you have software that uses the latest OpenSSL source code or alternative repositories.
How to patch#
As usual (ref: heartbleed , CVE-2015-0291 and CVE-2015-0286 ) with OpenSSL patches, it’s a 2-step fix. First, update the library on your OS.
$ yum update openssl
or
$ apt-get update $ apt-get install openssl
Then, find all services that depend on the OpenSSL libraries, and restart them.
$ lsof | grep libssl | awk '{print $1}' | sort | uniq
Since the attack is a man-in-the-middle attack, it’s advised to restart any service or application that communicates to a remote SSL/TLS endpoint.
If anyone manages to change either the DNS of your endpoint or modify the endpoint URL altogether, and point it to their own servers, your application may still accept it as a valid SSL/TLS stream.