I have a pretty old Synology NAS at home that I use for some basic file storage. I also abuse it as a cron-server, doing some simple rsync’s from remote systems. When I last tried to SSH into it, I was greeted with this error.
No matching ciphers found
$ ssh admin@nas.home Unable to negotiate with 192.168.126.100 port 22: no matching cipher found. Their offer: aes128-cbc,3des-cbc,aes192-cbc,aes256-cbc
Turns out my clients’ SSH was updated and was blocking several insecure ciphers by default. And this Synology runs an ancient SSH daemon, that only supports those ancient outdated ciphers.
Force a set of ciphers your client supports
To check which ciphers your client supports, run this:
$ ssh -Q cipher 3des-cbc aes128-cbc aes192-cbc aes256-cbc rijndael-cbc@lysator.liu.se aes128-ctr aes192-ctr aes256-ctr aes128-gcm@openssh.com aes256-gcm@openssh.com chacha20-poly1305@openssh.com
In this list are several ciphers that are supported by my ancient SSH server as well as the client, they’re just blocked by default on the client. Things like 3des-cbc, aes128-cbc, aes256-cbc, … etc.
To enable those ciphers anyway, you can force their use with the -c parameter.
$ ssh -c aes256-cbc admin@nas.home
This will re-allow access to that ancient SSH server.
Now to find a way to upgrade the SSH daemon on that Synology without breaking it …
Update: recent versions of Synology allow you to change this
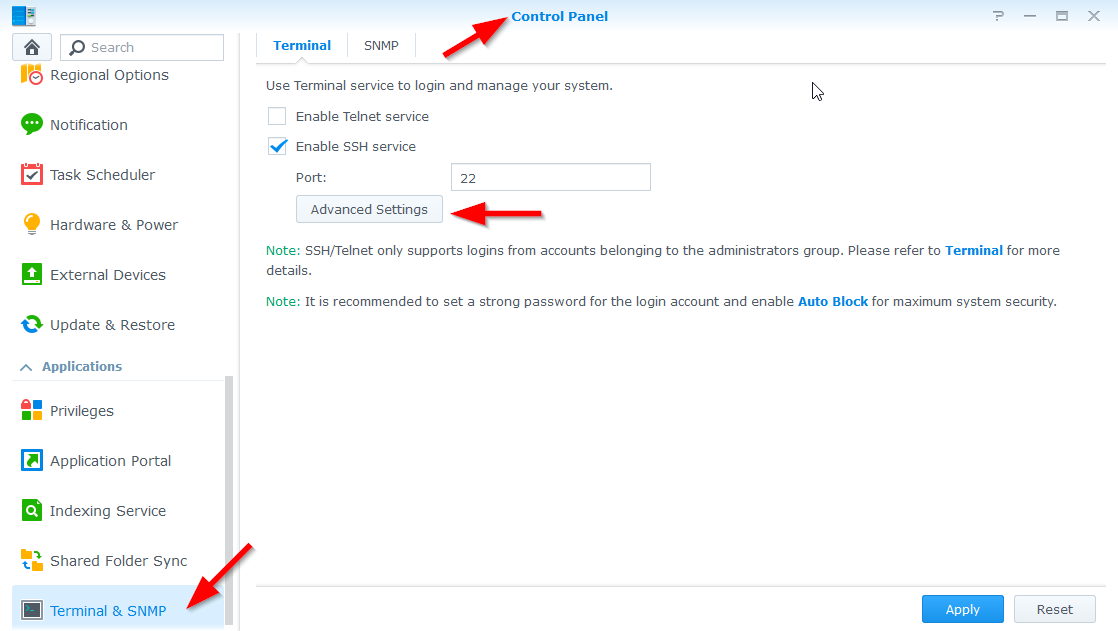
If your Synology is up-to-date, you can navigate to the Controlpanel > Terminal & SNMP > Advanced Settings.
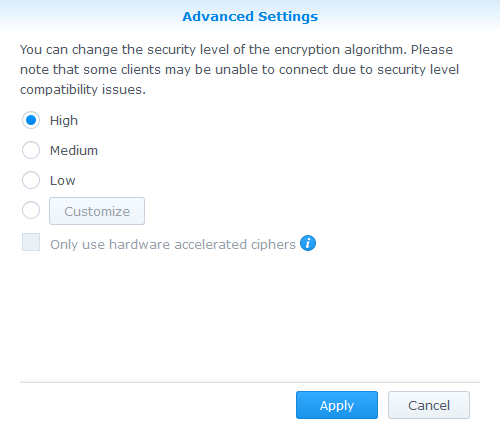
In there, pick the High advanced settings for the encryption algorithm.
Now give it a try again!