Jumphosts are used as intermediate hops between your actual SSH target and yourself. Instead of using something like “unsecure” SSH agent forwarding, you can use ProxyCommand to proxy all your commands through your jumphost.
Using SSH Jumphosts
Consider the following scenario.
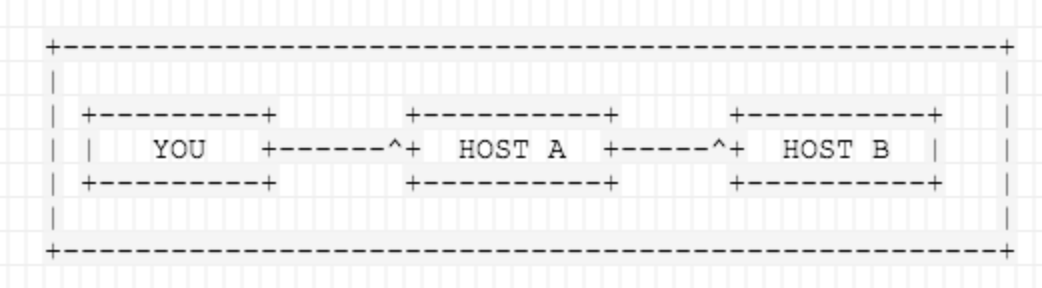
You want to connect to HOST B and have to go through HOST A, because of firewalling, routing, access privileges, … There’s a number of legit reasons why jumphosts are needed, not just preferred.
Classic SSH Jumphost configuration
A configuration like this will allow you to proxy through HOST A.
$ cat .ssh/config Host host-a User your_username Hostname 10.0.0.5 Host host_b User your_username Hostname 192.168.0.1 Port 22 ProxyCommand ssh -q -W %h:%p host-a
Now if you want to connect to your HOST B, all you have to type is ssh host_b, which will first connect to host-a in the background (that’s the ProxyCommand being executed) and start the SSH session to your actual target.
SSH Jumphost configuration with netcat (nc)
Alternatively, if you can’t/don’t want to use ssh to tunnel your connections, you can also use nc (netcat).
$ cat .ssh/config Host host-a User your_username Hostname 10.0.0.5 Host host_b User your_username Hostname 192.168.0.1 Port 22 ProxyCommand ssh host-a nc -w 120 %h %p
This has the same effect.
Sudo in ProxyCommands
If netcat is not available to you as a regular user, because permissions are limited, you can prefix your ProxyCommand's with sudo. The SSH configuration essentially allows you to run any command on your intermediate host, as long as you have the privileges to do so.
$ cat .ssh/config ... ProxyCommand ssh host-a sudo nc -w 120 %h %p
ProxyCommand options allow you to configure SSH as you like, including jumphost configurations like these.