tl;dr: if your site has any kind of login section, you'll want to switch to HTTPs. You should have done so a long time ago (security, privacy), but now Firefox is giving you even more of an incentive to do so.
This tweet brought it to the attention:
PSA: In Firefox 44 Nightly, "http:" pages with are now marked insecure. pic.twitter.com/qS9LxuRPdm
— Richard Barnes (@rlbarnes) October 20, 2015
If you have a form on your website where one of the fields is of the type="password", the page will now be marked as insecure in your browser if it is served over a plain HTTP connection.
Here’s what a normal, secure, page looks like with a type="password" input field.
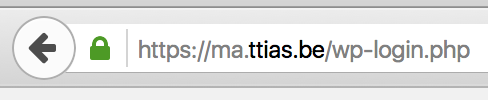
And here’s the new Firefox Nightly display of a similar page, but in plain HTTP (with a shameless plug to Senioren Digitaal , offering IT classes to elderly people).
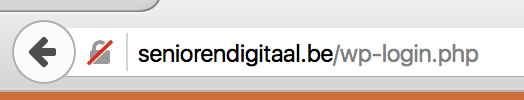
This change, once it makes it to the mainline version of Firefox (current Firefox is at version 41, nightly is at version 44), will make users even more aware of the dangers of submitting passwords to a plain HTTP website.
Every HTTPS/TLS connection can already show you more information in the security panel in Firefox . This warning is shown on plain HTTP connections where there is no Security Panel in the inspector.
If you hover over the warning, you’ll see more information on why the red indicator is shown.
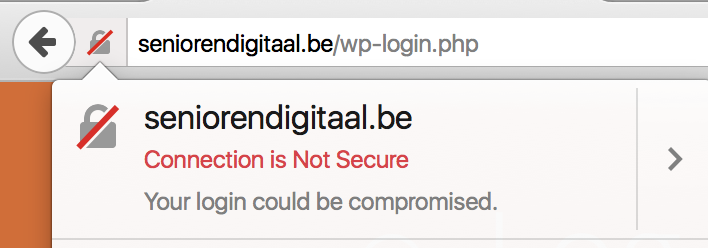
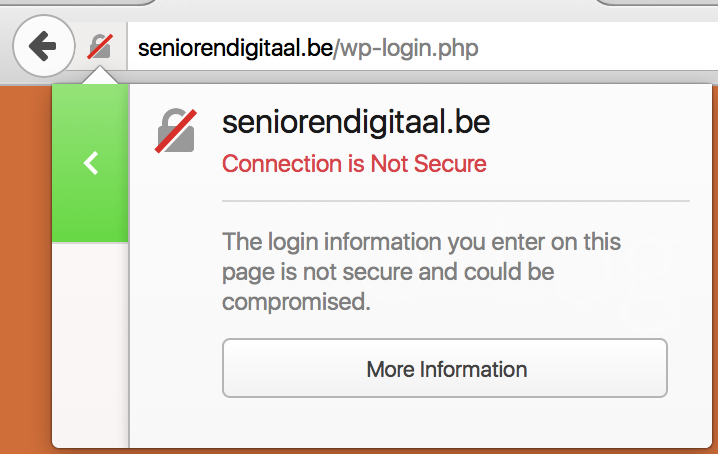
This move from Firefox comes after several discussions of marking HTTP connections as insecure by default . I believe it’s good UX to only show the insecure icon on pages where it actually makes a difference.
Yes, HTTPs everywhere would be a good idea. Privacy and eavesdropping are among the most important motivators. Security is a very nice side-effect.
But since not every website has a login section where passwords can be stolen, marking all HTTP connections as insecure wouldn’t be a good idea. It would just train users to see a red indicator in the upper left corner and consider that the new normal.
We’ve now got several ways of marking a connection as insecure, besides the usuals (expired SSL, invalid hostname, …) in multiple browsers:
- Password-fields in a plain HTTP site
- SHA-1 SSL certificates which expire after 2015
What are your thoughts on this?